Understanding the IT-to-Employee ratio: Its rise and repercussions
BetterCloud
APRIL 24, 2025
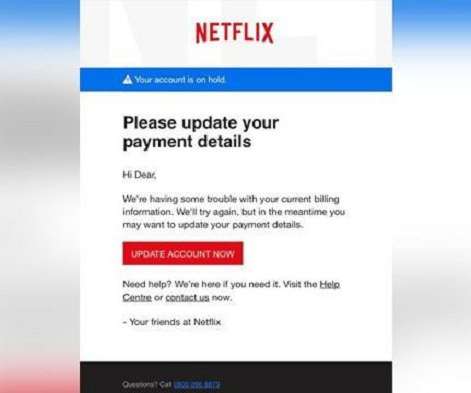
From governance and cybersecurity to data management and user support, the demands on IT departments are constantly escalating. Cybersecurity threats: The ever-evolving landscape of cyber threats necessitates robust security measures, demanding specialized expertise and constant vigilance from IT professionals. Save your seat.































Let's personalize your content