Why 36% is the magic number: Finding the right amount of text in mobile apps
Intercom, Inc.
JANUARY 21, 2020
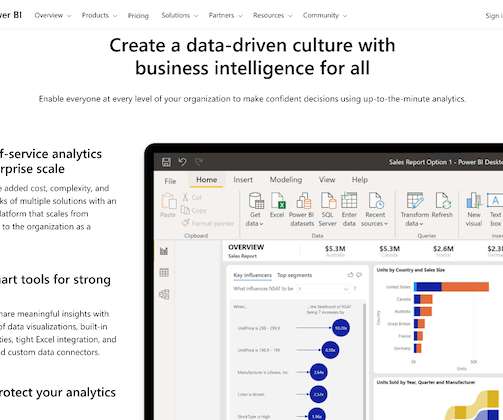
The results shows us the value of taking a principled approach to writing text for mobile apps – because product design is still all about the words. Mobile apps dominate our digital experiences. A quick Google search and a calculator tells me that’s an average 25 mobile apps for every person on Earth. Measuring the letters.










































Let's personalize your content