Top 12 information security recommendations for software companies with Embedded Payments
Payrix
FEBRUARY 22, 2024
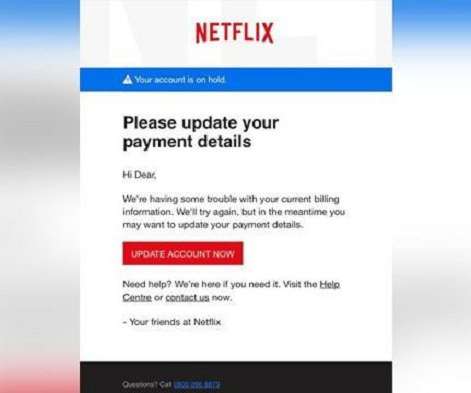
Twenty percent of those breaches were due to compromised credentials. How to prevent costly data breaches It’s crucial for software platforms with embedded payments to implement a multi-layered security approach that involves constant risk assessment, threat mitigation, and compliance with industry standards and regulations.














































Let's personalize your content