Technical Review: A Trusted Look Under the Hood
TechEmpower SaaS
AUGUST 21, 2023
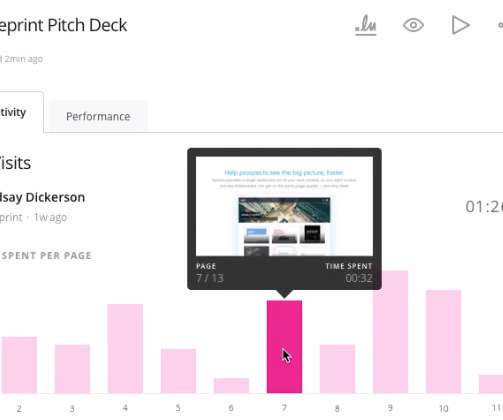
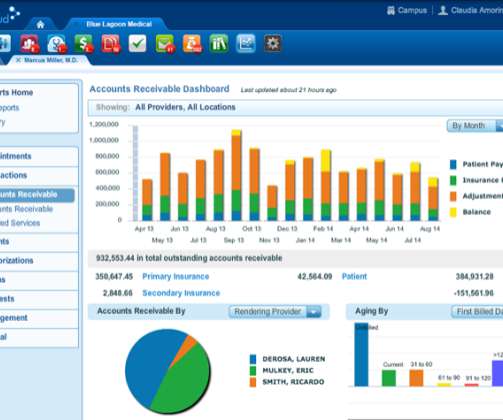
The answer is to engage a trusted outside source for a Technical Review – a deep-dive assessment that provides a C-suite perspective. At TechEmpower, we’ve conducted more than 50 technical reviews for companies of all sizes, industries, and technical stacks. A technical review can answer that crucial question.










































Let's personalize your content