SOC 2 Policies: What They Should Include and Why They Matter
Scytale
DECEMBER 10, 2024
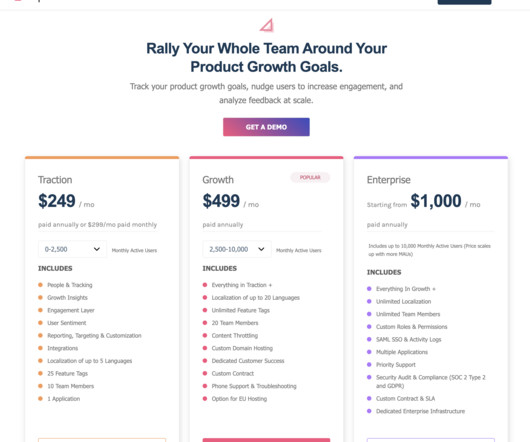
These policies form the basis of your SOC 2 control list, which auditors review to confirm youre meeting requirements. Scytale streamlined the process by providing expert-driven technology. Access Control Policy: Defines who gets access to what and ensures regular reviews. Our SOC 2 audit preparation was smooth sailing.






































Let's personalize your content