Market Gaps: 10 Ways to Spot Untapped Customer Needs
User Pilot
NOVEMBER 30, 2023
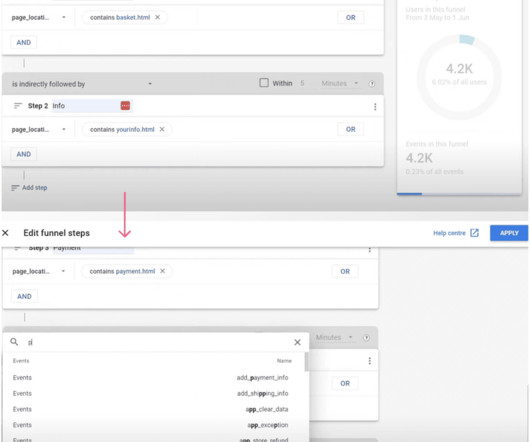
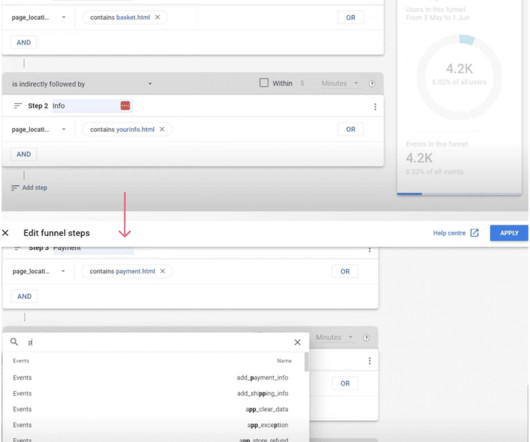
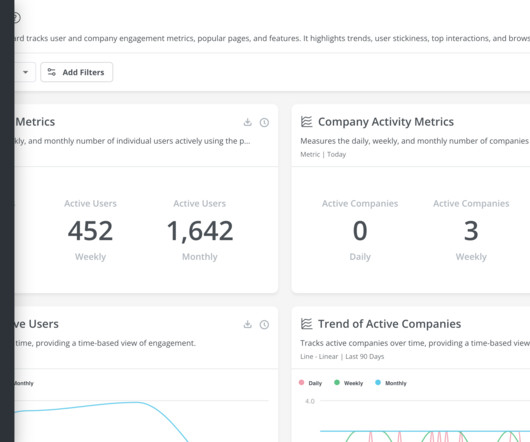
A market gap can be caused by missing functionality or poor user experience. Tracking user behavior in-app enables product teams to find ways to improve product experience. Competitor analysis enables PMs to find areas where rivals fail customers and develop sound positioning and differentiation strategies. Book the demo!
















































Let's personalize your content