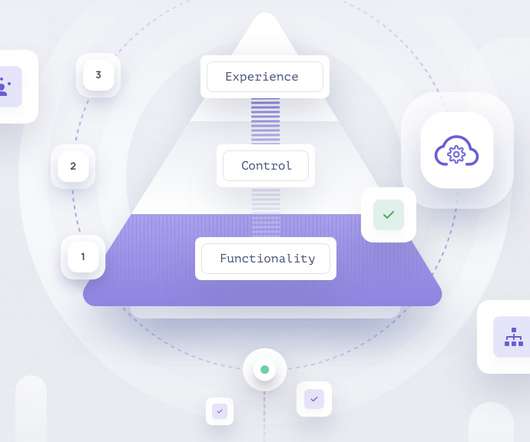
SaaS Product Readiness Pyramid
Frontegg
NOVEMBER 12, 2020
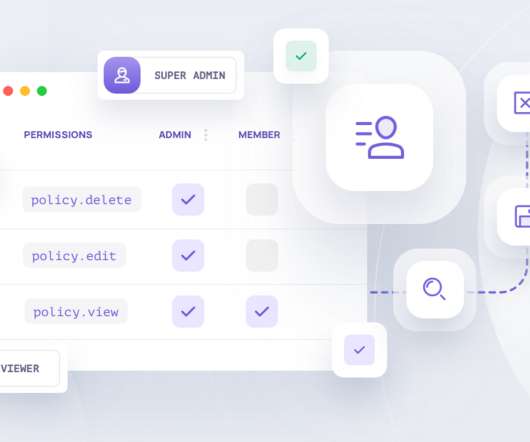
The state of mind here is important, we’re still not sure that this feature will become a standard in our product, so we would not want to invest too much effort into it. Not entirely, the control tier in this case could also be an external API with documentation. The post SaaS Product Readiness Pyramid appeared first on Frontegg.



















Let's personalize your content