Q&A recap: Driving customers to value during onboarding, at scale
ChurnZero
JULY 22, 2022
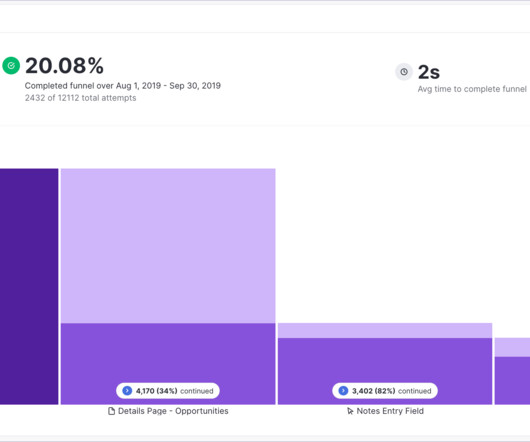
Does your Customer Success team have a shallow view of onboarding? Whether it’s greater efficiency, increased revenue, cost savings, or achieving compliance, every customer has a reason for purchasing your product. Q: Should the definition of first value be based on your team’s perspective or the customer’s perspective?











































Let's personalize your content