Pentest as a service for fast-growing SaaS companies
Audacix
AUGUST 17, 2022
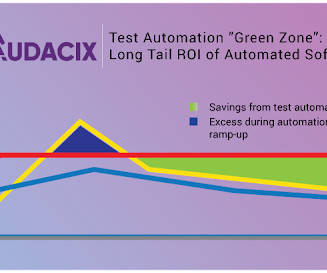
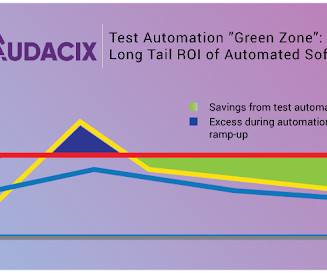
Until, of course, you stumble upon and adopt the pentest-as-a-service approach to security. This mindset demands that you have strong and flexible cyber security measures in place to safeguard your customers' data and mitigate the constantly growing list of security threats.




























Let's personalize your content