Why Should You Consider Application Security Automation?
Audacix
JANUARY 31, 2024
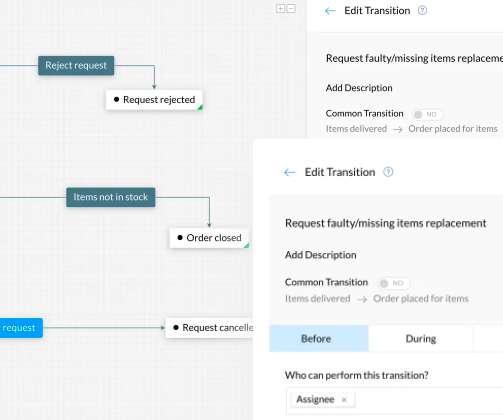
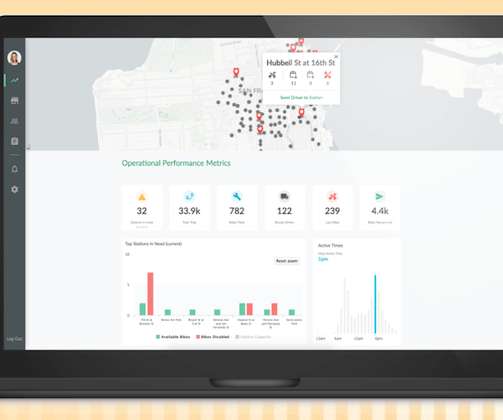
Automating application security processes is not just a technological convenience; it is a strategic necessity as cyber-attacks and security incidents keep getting more complex. Conducting manual application penetration testing for functional operations and security measures can often lead to delays in your software development lifecycle.




































Let's personalize your content