How To Do Software Security Testing Without Security Experts
Audacix
OCTOBER 18, 2023
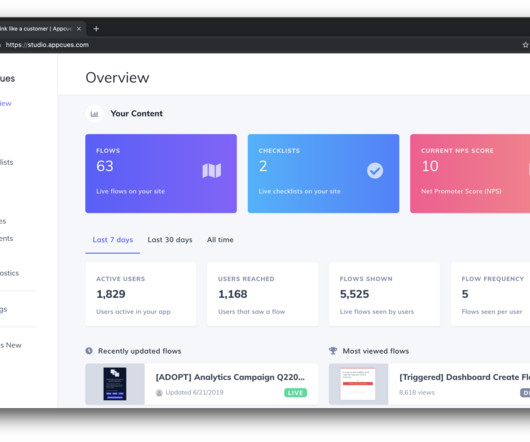
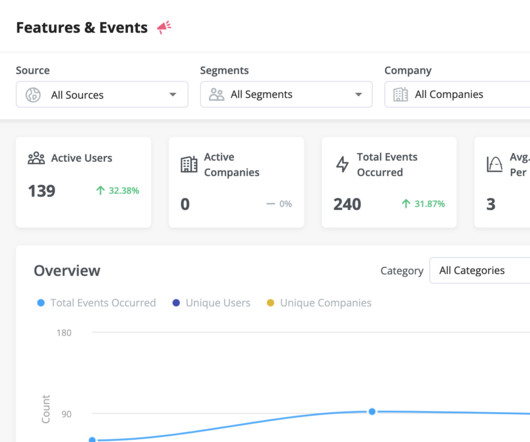
While functional software testing is already regarded as a critical component of the software development lifecycle, unfortunately, automated software security testing remains an afterthought for the majority of software teams. An automated web application security testing that you can use is Cyber Chief.

























Let's personalize your content