AI Reaccelerating Cloud Growth
Tom Tunguz
OCTOBER 23, 2023
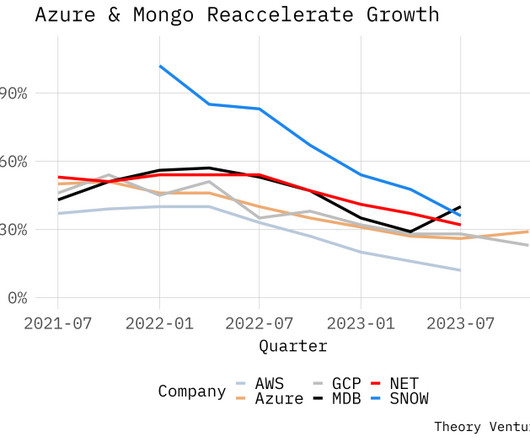
I’ve been tracking the growth rates of these companies and product lines for the last 18 months to develop a broad gauge of enterprise buying patterns after the downturn. “Because of our overall differentiation, more than 18,000 organizations now use Azure OpenAI service, including new-to-Azure customers.”






















Let's personalize your content