AI Reaccelerating Cloud Growth
Tom Tunguz
OCTOBER 23, 2023
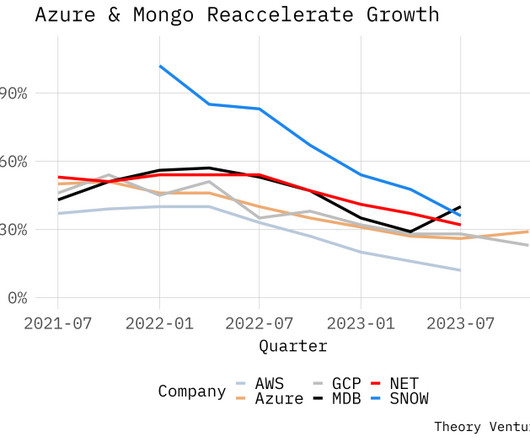
“Because of our overall differentiation, more than 18,000 organizations now use Azure OpenAI service, including new-to-Azure customers.” ” “Higher-than-expected AI consumption contributed to revenue growth in Azure.”

























Let's personalize your content