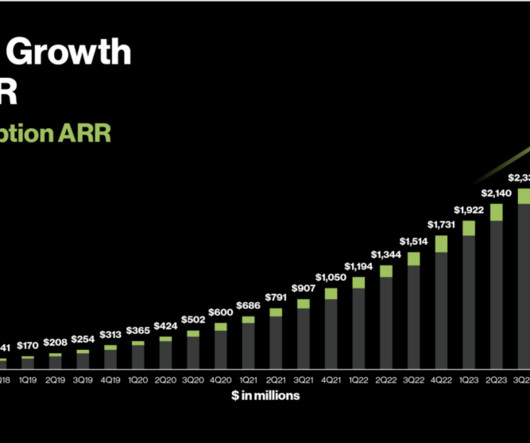
5 Interesting Learnings from Crowdstrike at ~$3 Billion in ARR
SaaStr
NOVEMBER 15, 2023
64% of Large Customers Sourced From Partners They are AWS’s largest cybersecurity partner. Most Enterprises Buy More Than 60 Endpoint Security Products So there is room for many winners here. #8. What’s your channel / partner strategy? #9. Only Founded in 2011.


































Let's personalize your content