Partnering with Dropzone: Automating Security Operations with AI
Tom Tunguz
APRIL 24, 2024
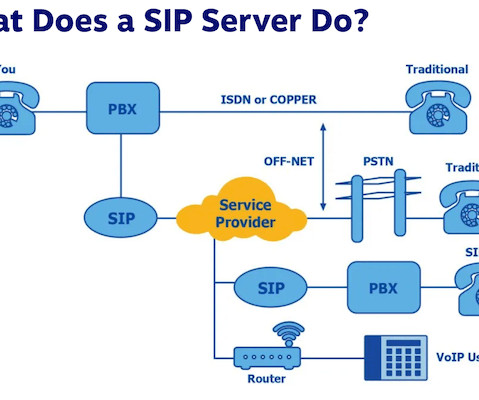
Enterprises spend more on security but aren’t benefitting from the extra spend. Palo Alto Networks’ customers who buy security across 3 platforms spend more than 40x those that secure just one. ” - Nikesh Arora, CEO of Palo Alto Networks The average enterprise uses upwards of 70 security products.










































Let's personalize your content