As a software engineering leader, you know application security is no longer an activity that you can palm off to someone else.
With the increasing number of sensitive data security breaches, it's essential to have the right automated application security tools in place to protect your software.
Today I'll introduce you to developer-focused security tools like Dynamic Application Security Testing (DAST) and Static Application Security Testing (SAST) tools and others that will help you automate security.
Then I'll go further and tell you about 12 of the best options for your team.
Don't worry if you're not a cybersecurity expert; I'll break it down for you in no-BS, simple terms. Plus, you'll get real-world examples to help you understand the key concepts.
How do you secure an application software?
To enhance your application security posture, it's essential to have a comprehensive security structure in place.
But what does that mean? What does that "structure" look like?
The security testing structure that I'm recommending to you below is exactly the same that I advise our clients to put in place. It helps you automate application security testing and cloud security validation so that you can reduce your reliance on external consultants and security teams.
Following my advice in its entirety will place you in the top 8-9% of software teams globally from an application security perspective.
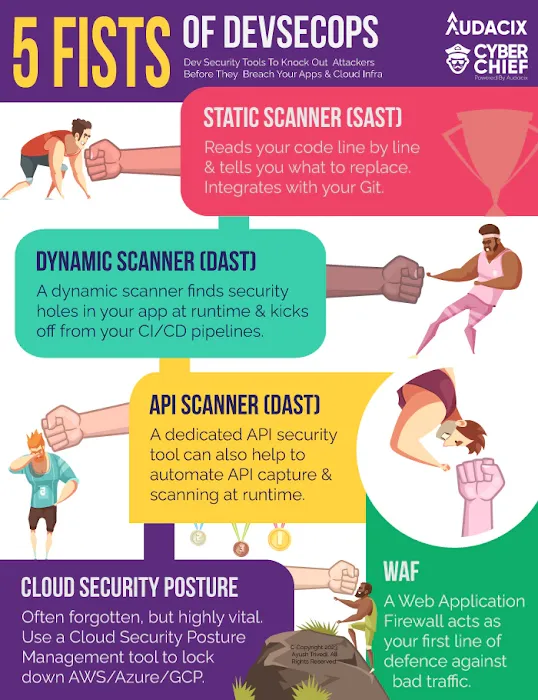
I've named this structure the "5 Fists of DevSecOps".
Why "Fists"? Well, the 5 Fists are a set of automated tools that allow you to beat hackers into submission so that they give up on trying to attack your application and cloud infrastructure.
Think of the 5 Fists as a "minimum" application security structure that allows you to automate the protection of your application, APIs and cloud network infrastructure.
These application vulnerability scanners and network-related security tools work together to give you a multi-layered defense against various types of threats and vulnerabilities.
Static Application Security Testing tools (SAST)
SAST application security tools analyze your source code to identify potential security vulnerabilities during the development process. This helps you catch and fix issues early on, before they become a part of your application.
The best static analysis tools also provide software composition analysis (SCA) capability. SCA is a methodology to help your team find vulnerable open source code or repositories in your software applications.
If you select the right SAST tool, you won't have to add a different tool to your stack to perform software composition analysis tests.
Dynamic Application Security Testing tools (DAST)
Dynamic analysis tools provide web application scanning during runtime of your software. Therefore, they're able to simulate real-world attacks to uncover security flaws. These vulnerability testing tools helps you identify vulnerabilities that may not be apparent during static code analysis.
Keep in mind that the best DAST scanning tools also help you fix and detect vulnerabilities in your SOAP, REST and GraphQL APIs.
This type of automated penetration testing tool is invaluable if you have an API-heavy or single-page web applications.
Only the best DAST products provide automated tools to help you catalogue your APIs so that you never forget to test an endpoint and so that your API management burden also reduces.
Web Application Firewalls (WAF)
WAF tools provide an additional layer of security by protecting your applications from common web exploits, such as SQL injection and XSS attacks.
By using a combination of SAST, DAST, and WAF tools, you can ensure that your applications are secure from the ground up and protected against a wide range of threats.
Cloud Security Platform Management (CSPM)
Microsoft defines a CSPM tool as one that "identifies and remediates risk by automating visibility, uninterrupted monitoring, threat detection, and remediation workflows to search for misconfigurations across diverse cloud environments/infrastructure, including: Infrastructure as a Service (IaaS)."
Want a simpler explanation?
CSPM application security tools help you lock down your cloud consoles and associated assets and workflows - apart from your application and APIs - so that you don't provide an easy backdoor for hackers.

Why do I need all of these AppSec tools?
While SAST, DAST, and WAF tools may seem to protect against the same types of OWASP Top 10 vulnerabilities, they each serve a unique purpose and provide different layers of protection.
Using all 3 types of application security tools ensures a comprehensive approach to application security that will allow you to claim that you have "best-practice application security controls" in place.
But let me give you real-world examples of why all of these tools are necessary:
-
SAST tools focus on identifying vulnerabilities in the source code during the development process. They help you catch issues early on, before they become a part of your application. However, SAST tools will not help you find vulnerabilities that only become apparent during runtime or in the application's environment.
-
DAST tools scan your applications during runtime, simulating real-world attacks to uncover security flaws. They can identify vulnerabilities that SAST tools might miss, such as those related to configuration or deployment. However, DAST tools will not be able to detect issues in the source code itself.
-
WAF tools provide an additional layer of security by protecting your applications from common web exploits, such as SQL injection and cross-site scripting (XSS) attacks. A WAF acts as a barrier between your application and potential attackers, helping to prevent exploitation of known vulnerabilities. However, WAF tools cannot fix the underlying issues in your code or application environment.
-
Don't forget that only a CSPM tool can perform security testing on your cloud platform - so it's a must-have component of this application security structure.
Want a real-world example?
Your web application probably uses a (or many) third-party library with a known vulnerability in which case a SAST tool might detect the vulnerable library in your source code repositories during code analysis, but it cannot protect the application from an actual attack exploiting that vulnerability.
A DAST tool will identify the vulnerability during runtime, but it cannot prevent the attack from happening - it can only help you minimise the damage.
A WAF, on the other hand, can block some attacks by filtering out malicious requests targeting the known vulnerability.
Using all three types of tools, you can identify the vulnerability, understand its potential impact, and protect your application from exploitation.
Think of it like protection for your house:
The front fence is your CSPM tool;
The security door in front of your main door is your WAF;
The biometric digital lock on your main door is your DAST tool; and
The cameras inside your house is your SAST tool.
Why have you not included interactive application security testing?
Great question! Interactive application security testing tools are typically used during a traditional functional software testing process and don't necessarily conduct security testing on your entire application.
The selective nature of interactive application security testing application security tools makes it unsuitable for fast-pace software development lifecycle environments because it adds extra burdens in terms of in-house security testing skills, or at least extensive security testing training.

Which businesses benefit most from application security tools?
If your company has an in-house or outsourced software team and you need to protect sensitive data and minimize security risks then you will benefit from the cloud and web application security tools that I've listed here.
Remember, these are not "nice-to-have" application security tools. The tools I've recommended below are will help you minimize the risk of security incidents in all your application environments, particularly your production environment.
How I selected these 12 tools
The rationale for selecting these nine tools is based on the challenges faced by software teams when implementing and using application security tools. These challenges include ease of use, setup complexity, training/experience required, and other relevant factors.
The tools that I've inlcuded in this article address these challenges and provide a comprehensive solution for software engineering teams and leader looking to enhance their application security posture.
These are some of the factors I considered when selecting these application security tools:
-
Ease of use: The tools should have user-friendly interfaces and provide clear, actionable insights to help software dev managers understand and address security issues.
-
Setup complexity: The tools should be easy to set up and integrate with existing development processes and tools, minimizing disruption to your team's workflow.
-
Training/experience needed to operate: The tools should be accessible to software leaders and their teams with little cybersecurity knowledge, providing guidance and support to help them effectively use the tools.
-
Scalability and adaptability: The tools should ideally be a cloud-based solution be able to grow with your team and adapt to changes in the application security market, ensuring that your application security testing capabilities remain strong as your needs evolve.
-
Integration options: The tools should offer integration with popular tools and platforms utilised in your software development lifecycle, making it easier for your team to incorporate them into their existing processes.
-
Pricing and support: The tools should offer a range of pricing options and provide strong customer support to help you address any issues that may arise.
Best DAST tool: Cyber Chief
Cyber Chief is a powerful application security platform that helps you identify thousands of vulnerabilities in your web applications, API endpoints and cloud platforms.
It scans your web applications, APIs and cloud platform during runtime, simulating real-world attacks to uncover security flaws.
This means that it actually access your application through a browser. It will also login to your application to find vulnerabilities behind your login, because that's where most of your critical vulnerabilities will exist.
With its user-friendly interface, best-practice application security fixes, intuitve dashboard and comprehensive security testing reporting, Cyber Chief makes it easy for software engineering leaders to understand and address security issues without having to spend endless amounts on security training for their developers.
Benefits of Cyber Chief as a dynamic application security testing tool:
-
Detects a wide range of vulnerabilities, including the OWASP Top 10, SANS CWE 25 and
-
Offers continuous monitoring and automated scanning with smart identification of false positives to save you time
-
Integrates with popular development tools like Slack, Jira and Jenkins
-
Intuitive dashboard to help you quickly analyse your application security posture in real time so that you can make data-driven decisions
-
Unparalleled vulnerability management with detailed fixes, including code snippets to save your developers a truckload of time
-
Fast API endpoint testing for teams that have API-heavy or mobile apps
You can quickly see why this is a vulnerability scanning tool that is fit to be used by non-cybersecurity experts, like your software developement team, right?

Other DAST tools
Acunetix (paid tool)
Acunetix is another popular application security tool that specializes in web application security. It scans your web applications for vulnerabilities and provides detailed reports to help you prioritize and fix issues.
Acunetix is known for its speed, making it a popular choice among security teams that have lots of experience and accreditations. However, it's use as an application security software for non-security testing experts is often debated and there are Acunetix alternatives that are more suited for this purpose.
Benefits of Acunetix application security testing tool:
-
Detects over 7,000 vulnerabilities, including OWASP Top Ten risks
Offers integration with popular issue trackers and CI/CD tools
Provides some insights and remediation guidance
Has good flexibility for application security testing experts
OWASP ZAP (open-source)
OWASP ZAP (Zed Attack Proxy) is a free, open-source DAST tool developed by the OWASP community. It's designed to help you find security vulnerabilities in your web apps by simulating attacks during runtime.
ZAP is an easy option for software teams looking for cost-effective application security tools.
Naturally, free tools have their own hidden integration and maintenance costs compared to paid tools, and this is true for application security tools like Zap too.
Reviews as reported by its online community:
It's free, but this also means that it lacks support
Supports a wide range of authentication mechanisms
Offers an extensive range of plugins and add-ons
-
Active community support and regular updates, but these updates can be buggy thereby reducing your utility of the tool
Best SAST tool: Snyk
Snyk is a static application security tool that focuses on identifying and fixing vulnerabilities in open-source dependencies.
It scans your codebase and alerts you to any security risks in the libraries and frameworks you're using.
Snyk is a valuable tool for a software engineering manager like you who wants to ensure their web applications are secure without compromising on the benefits of open-source software.
Benefits of Snyk during our useage:
Supports a wide range of languages and package managers
Offers continuous monitoring and automated remediation
Integrates with popular SDLC tools and platforms
-
Also performs software composition analysis functions with an up-to-date database
-
Best in class vulnerability management features for static analysis tools

Other SAST tools
Mend.io
Mend.io is a static application security software that analyzes your source code to identify potential security vulnerabilities. It's designed to integrate seamlessly with your development process, providing real-time feedback and actionable insights.
Mend.io is a good choice for software development managers who want to ensure their code is secure from the ground up.
Benefits or Mend include:
Supports multiple programming languages and frameworks
-
Offers integration with popular development tools and platforms
Provides detailed reports and remediation guidance
-
Has improved customer service after recent rebrand and restructure
SonarQube
SonarQube is a popular static application security program that helps you maintain code quality and security.
SonarQube is a good choice for software teams who want to ensure their applications are secure and maintainable.
Benefits of SonarQube include:
Supports over 25 programming languages
Offers integration with popular CI/CD tools and platforms
Provides customizable quality profiles and rules
Best WAF tool: Cloudflare
Cloudflare is a popular "freemium" Web Application Firewall (WAF) that provides an additional layer of security for your web applications and APIs.
It protects against a wide range of threats, including DDoS attacks, SQL injection, and cross-site scripting (XSS). Cloudflare is an excellent choice for software dev teams looking for a comprehensive security solution that's easy to implement.
Benefits:
Global network with fast performance
Customizable security rules and settings even on the free plan
Integrates with popular platforms and tools
Great documentation and setup time is minimal
-
Cloudflare Workers is a great edge computing feature that can do simple things like serve consisent HTTP security headers across your environments or even host entire websites with blazing speed
Other WAF tools
AWS WAF
AWS WAF Amazon Web Services' very own WAF and integrates well with assets that run on its platforms.
It's designed to protect your web applications from common web exploits and allows you to create custom rules to block specific types of attacks.
AWS WAF is a great option for software and DevOps teams that are already using AWS services or looking for a scalable and flexible WAF solution.
Benefits of staying in AWS's ecosystem:
Pay-as-you-go pricing model that comes to you in one bill
-
Easy integration with other AWS services so the learning curve is usually not as steep
Real-time metrics and monitoring
Qualys Cloud Platform
The Qualys Cloud Platform is a older brand that provides vulnerability assessment tools as well as a WAF that offers features to protect your applications from a wide range of threats.
It uses machine learning and behavioral analytics to detect and block attacks in real-time.
Qualys may be a decent choice for enterprise software teams looking for a robust and reliable WAF solution. However, it's designed to be used in conjunction with in-house security teams so may not be a good fit if your organisation doesn't have this capability.
Benefits of Qualys:
Advanced threat detection and mitigation
Scalable and adaptable to your needs
Comprehensive reporting and analytics
Best CSPM tool: Cyber Chief
Remember how I said Cyber Chief was a "3-in-one" application security testing tool?
Well CSPM is one of the prongs that makes Cyber Chief so powerful and a very well-rounded tool for many of your cloud app security needs.
The key features and benefits of Cyber Chief's Raider CSPM application security feature include:
-
Cloud-agnostic so works across AWS, Azure and Google Cloud Platform
-
Runs CIS benchmarking checks to help you implement best-practice cloud security controls and be alerted when the wrong configurations are set
-
Helps you stay compliant with 20-odd frameworks including ISO27001 certification, SOC 2 certification, GDPR, CCPA and other compliance frameworks
-
5-minute setup that your DevOps teams or software developers can do themselves
-
Scheduled automated testing so that you never have to manually run a scan
-
Dedicated client success manager to help with training and technical support

Other CSPM tools
Palo Alto Prisma Cloud
Prisma Cloud is a CSPM solution that provides visibility, threat detection, and compliance monitoring across multi-cloud environments.
It helps some large enterprises maintain a strong cloud security status by identifying and remediating misconfigurations, monitoring user activity, and detecting threats in real-time.
Benefits:
-
Supports multi-cloud environments, including AWS, Azure, and Google Cloud Platform
Provides continuous monitoring and automated remediation
Offers integration with popular CI/CD tools and platforms
-
Includes advanced threat detection and machine learning capabilities
Sophos CSPM
Sophos CSPM is a cloud security solution that helps large organizations monitor and manage their cloud environments to ensure security and compliance.
It provides visibility into cloud assets, detects misconfigurations, and helps enforce security policies across multi-cloud environments.
Benefits:
Supports AWS, Azure, and Google Cloud Platform
Offers continuous monitoring and automated remediation
Provides customizable security policies and templates
Includes compliance reporting and auditing capabilities
How to choose the right application security tool for your software team
When selecting the right vulnerability scanning tool with automation capabilities for your team, consider the following factors as you take in the demos of multiple tools:
-
Assess your team's specific needs and requirements, particularly in relation to the app security expertise within your team
-
Evaluate the ease of integration with existing tools and processes
-
Consider the tool's scalability and adaptability to future growth of the application security landscape
-
Compare pricing and support options and be wary of tools that ask you to commit to multi-year subscriptions
-
Consider whether you want one tool like Cyber Chief that peforms multiple cloud security testing functions very well or whether you're comfortable having multiple tools in your application security tools stack.
Can I start for free with Cyber Chief?
The answer is yes. Start your free Cyber Chief account today.
Or if this is all still too overwhelming and you need someone to guide you through your choices in a no-pressure environment, set up a discovery call with my team and you'll be able to understand the options that are best for your unique situation.