Adding good vulnerability testing tools or virtual app scanning for your software team has become as important as your git repository or your ticket management system.
So the big questions are, which one will work for your software development:
1. Without creating extra delays in your application delivery schedule; and
2. Without creating extra costs related to managing a new tool?
Naturally, costs (or philosophical considerations) might compel you to choose the open source path.
But then you're at the mercy of the expedience of community members to fix bugs and release new features.
You might end up building a whole team in-house to support the open source tool of your choice, which, one would think, defeats the purpose of going open source in the first place?
A commercial vulnerability assessment tool comes with lots of benefits but may also have some element of "lock-in," which might trouble you, among other aspects of having to deal with a new vendor.
In this article I've only considered web app vulnerability scanning tools. Mobile app or IoT vulnerability testing tools are at this stage only designed to be used by cybersecurity experts and cannot reliably be integrated into you a DevOps software deployment pipeline.
So now, let's start with the different types of application vulnerability assessment tools that are available to you.
What are the different types of vulnerability scanners available?
The biggest misconception with vulnerability scanners is that people assume that one tool can help you with all your vulnerability management needs.
Let me debunk this myth for you: a network vulnerability detection tool like a web application firewall (WAF) or endpoint security tool cannot help you find and fix vulnerabilities in your web applications and APIs, despite their claims.
Just like a surgeon has different scalpels for different surgeries, you need different scanning tools depending on what you are scanning.
Web application vulnerability scanners
Application vulnerability scanners automatically scan web applications and web servers to find OWASP Top 10 vulnerabilities like SQL injection, insecure configurations in your server, cross-scripting and others.
The best web application vulnerability scanning tools log into your application to scan behind the login.
This is important because we know that 93% of your vulnerabilities are found behind the login.
API vulnerability scanner
APIs rule the world irrespective of whether you're building a modern application or trying engaged in a digital transformations of legacy applications.
API vulnerability scanners not only help you with scanning vulnerabilities in your REST, SOAP and GraphQL APIs, but the best vulnerability scanners for APIs also:
- Help you discover all API endpoints
- Make it easy to produce configuration files in OpenAPI or Swagger format
- Perform automated vulnerabiilty assessment on your APIs daily without having to employ someone to operate the scanning tool.
- Help your minimize the chances of shadow APIs creeping into prod.
- Work alongside a powerful web vulnerability scanner to put your application security on autopilot, without being forced to hire expensive security experts.
Good API vulnerability assessment tools work like a baseline security analyzer and give you results that you can rely on and benchmark whether your application is cloud-based or on premises.
Network vulnerability scanners
When performing this type of vulnerability management you can assess your wired and WiFi network security controls and network appliances like routers and firewalls.
They also help to keep out unauthorized devices from a business network.
When you perform such network vulnerability tests, you can identify current devices and users in your network and take inventory of your network elements.
Cloud platform vulnerability scanning tools
Most businesses are shifting to a cloud-based model and using cloud infrastructure for their applications and APIs because of higher flexibility and scalability.
This cloud infrastructure also needs to be secured. That's why vulnerability management using cloud platform vulnerability scanning tools will help you find and fix security threats like:
Poorly configured IAM policies.
-
Publicly exposed resources that should be very private (think S3/Blob buckets).
-
Configuration compliance issues that is used in compliance reporting for ISO27001 certification or SOC2 certification.

Can all vulnerability scanning tools find security vulnerabilities in software?
The short answer is no - not all vulnerability assessment scanning tools can find every security vulnerability in the software.
And let's be honest if any tool claimed to do so, it would be like a chef claiming they can make a perfectly cooked steak every time - sounds too good to be true, right?
While some vulnerability testing tools are designed specifically to scan for vulnerabilities in web applications and APIs, others only perform network vulnerability scanning as I explained earlier.
Network vulnerability scanners are typically used to detect and assess your WiFi security and vulnerabilities in your network infrastructure, such as firewalls, routers, and servers. They cannot log in to your web application or authenticate with your APIs and find vulnerabilities in your software as a logged-in user.
Remember the infamous Equifax data breach in 2017?
Well, it turns out that the vulnerability that led to the breach was actually known and could have been prevented if the right vulnerability scanner had been used.
What are the benefits of using vulnerability assessment scanning tools during software development?
Let me ask you this: is it better to stay fit and in the correct weight range throughout your life or only after your doctor tells you that you're overweight and at risk of serious diseases?
Similarly, if you run an application security process as an afterthought, you will be left with this problem:
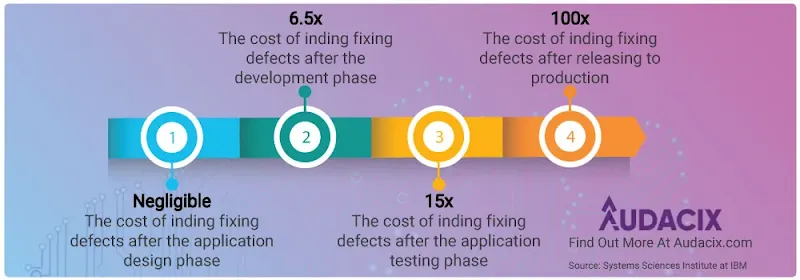
It'll take your team longer to untangle the vulnerabilities and they'll have to rewrite more code. All of this costs more time, therefore money.
It also leaves your application vulnerable for longer to many OWASP Top 10 vulnerabilities:
Cross-Site Scripting (XSS)
XSS occurs when a hacker loads malicious code in a web application from an external and unauthorized server.
Users of web applications compromised by this won't even know what's happening and can not only expose sensitive data but also ruin your app's user experience.
Code Injection
when there are missing updates or the web applications are vulnerable attackers can execute harmful codes. This is known as code injection which enables an attacker to take control of a business system once a user executes the code.
For example, a hacker can inject an SQL statement that always directs users to a specific table. This can allow access all customer-sensitive information and spoof identities in virtual environments.
Executing Arbitrary Commands
Attackers submit malicious input to a system that will execute arbitrary commands with the aim of taking control of an application.
After executing these commands they perform harmful activities like installing malware or deleting files that will affect everything from operating systems to APIs to databases and eventually affect business operations.
Buffer Overflow
A buffer overflow allows attackers to execute malicious code when a program tries to store excess data in the memory. The excess data can overwrite some parts of the memory and execute a harmful code.
For example, if you input data that's 10 bytes in a memory space that's only 8 bytes long there will be an overflow of 2 bytes. Such security risks can be difficult to handle but with the right mitigation techniques, you can avoid them.
Password Vulnerabilities
using weak passwords compromises critical business assets. When employees or team members use default passwords or passwords that hackers can quickly guess, it leaves systems vulnerable.
Lack of Encryption, Authorization, and Authentication
When you store or transmit data without encryption it poses a risk. Malicious actors can intercept such data or steal it from the database.
Another method hackers use is exploiting authorization and authentication weaknesses in systems. For example, poor access control or abusing session privileges can make web servers and other web applications vulnerable to attacks.
The good news is that most of these security issues can be prevented with a regulat vulnerability assessment, in between your periodic web application penetration tests.
How application vulnerability scanning tools identify and mitigate risks
Application vulnerability scanning employs a combination of techniques such as static analysis, dynamic analysis, and pattern matching, to uncover vulnerabilities.
For instance, a complete vulnerability assessment tool like Cyber Chief starts by crawling the application, exploring various paths and functionalities. During this process, it collects information about inputs, outputs, and potential attack vectors.
Next, the tool performs dynamic analysis by interacting with the application and simulating various attacks. It sends crafted requests to inputs, monitors the responses, and analyzes the behavior of the application under different scenarios. By doing so, it can detect vulnerabilities like cross-site scripting (XSS), SQL injection, or insecure access controls.
Additionally, static vulnerability scanning tools leverage pattern matching techniques to compare application components against known vulnerabilities, such as outdated libraries or frameworks. They reference comprehensive vulnerability databases, such as the Common Vulnerabilities and Exposures (CVE) list, to identify potential matches.
By combining these techniques, application vulnerability scanning tools can effectively uncover security gaps in an application, helping software engineering managers proactively address them before they are exploited by malicious actors.
How often should I run a web vulnerability scanner on my web applications and APIs?
Well, if your web application is actively developed by a team of developers with new code being pushed daily then you should be doing a daily automated vulnerability assessment.
If your application is not actively enhanced or altered, you can afford a vulnerability management structure that happens more irregularly.
But the real point is that the best vulnerability assessment scanning tools don't charge you for peforming more scans. So why not do more scans rather than fewer scans?
8 factors that decide the best software vulnerability assessment scanning tools
Even systems that seem secure have vulnerabilities.

Some of these vulnerabilities are obvious, and you can fix them quickly while others are serious issues and need more complex security patches.
-
Type of vulnerabilities: The tool should be able to detect all OWASP Top 10 and SANS CWE 25 vulnerabilities.
Don't be fooled by lesser tools that advertise "we test for 100,000 vulnerabilities" because most of them don't even apply to cloud applications and API, which means that a vulnerability assessment from such tools could lead to many false positives.
-
Scope of testing: The tool should be able to test the entire software stack, including front-end, back-end, and middleware components, to ensure comprehensive testing coverage.
-
Integration capabilities: The tool should be able to integrate with other tools and systems used in the organization, such as continuous integration/continuous delivery (CI/CD) pipelines, bug tracking systems, and security information and event management (SIEM) tools.
-
Reporting and analytics: The tool should provide comprehensive reports and analytics that enable software engineering managers to understand the severity of vulnerabilities and prioritize remediation efforts.
-
Ease of use: The vulnerability assessment tool should be user-friendly and easy to set up, configure, and use, even for non-security experts. An easy-to-use vulnerability scanner means you will take less time to identify and correct security vulnerabilities.
It also means the vulnerability assessment tool does not require you to have extensive knowledge or training before using it,.
-
Security patches: The vulnerability scanner that's right for your team is one that gives your software developers on-the-job coaching about how to patch vulnerabilities.
This type of web application vulnerability tool will not only help you upgrade your security process but also save you a truckload of money on formal security training.
-
Training and experience: Any vulnerability scanner that requires your software team to attend a training session to learn how to use it is probably not a good use of your time or money.
Your devs have enough to do. Why burden them with having to sit through training to learn a new tool? They'll start to resent it and probably won't ever use it to run vulnerability scans.
-
Support and documentation: The tool vendor should provide adequate support and documentation to help software engineering managers set up and use the tool effectively. Unfortunately, this is where many open source app scanning tools fall short with their vulnerability tests.
-
Accuracy and false positive rates: The vulnerability scanning tool should have a high accuracy rate in detecting vulnerabilities while minimizing false positives to avoid wasting time on unnecessary security measures and overheads.
False positives can be overwhelming to a network configuration manager when filtering false positives. An accurate vulnerability scanning tool can avoid such pointless vulnerability analysis tasks and save your team tons of time.
Best paid tool for vulnerability assessment scanning?
Cyber Chief
Cyber Chief is the best-paid web application vulnerability scanning tool in my opinion and that of thousands of software professionals around the world. It performs automated security scans of your:
Web applications, including by logging into your application
APIs, including automated API discovery
-
Cloud platform, to keep your AWS/GCP/Azure platform secure and compliant
Cyber Chief Pros
It includes an intuitive vulnerability management system that will enable you to provide comprehensive and automated on-the-job coaching to your developers about how to patch reported vulnerabilities.
Clear reporting enables you and the computer emergency readiness team to quickly handle the vulnerabilities identified.
Cyber Chief is a complete vulnerability assessment tool that performs web application security tests without you having to rely on any external security consultants.
It will free up your in-house security auditing team, if you have one, to concentrate on critical issues because it would have already helped your developers fix the "lower hanging fruit."
Because Cyber Chief is designed to be used by developers with zero security training and migration is free, it's a 3-in-1 vulnerability scanner that doesn't come with the overheads required for other tools.
Also, if you have an automted CICD code deployment pipeline then you will love Cyber Chief's "zero-click" vulnerability scanning feature that will produce a report for your team without anyone ever having to login to the tool.
Cyber Chief Cons
It doesn't have all the flexibility that many security experts require during a vulnerability assessment. This has been done deliberately because for software teams more flexibility means extra time wasted on training and critical vulnerabilities not being identified because of misconfigurations.
Plush if you have SOC 2 certification and/or ISO 27001 certification then Cyber Chief's Raider cloud platform scanning feature can help you stay compliant and keep your platform secure at the same time.

Other paid vulnerability scanning tools
Tenable.io
Pros
- Good network scanning capability with the Nessus/Tenable network security add-on.
- Tenable is best for your computer emergency readiness team working in-house.
- Frequent updates will present you with new key features.
- Its predecessor, Nessus, is the vulnerability scanning tool of choice for experienced application penetration testers who need minute configuration ability.
Cons
- The dashboard is not satisfactory, especially for such a popluar vulnerability tool.
- This network auditing tool is more expensive than others.
- Very hard to perform gray-box web application vulnerability assessment scans.
- Needs lots of training and experience to run meaningful vulnerability scanning and therefore isn't the best fit for most software teams.
Netsparker/Invicti
Pros
- User interface has improved as has the automation feature.
- You can perform a limited amount of API vulnerability scanning during a network auditing process.
- Has a stand-alone license that you can use on each machine, but this often means your laptop will be out of action for hours at a time while the vulnerability assessment is taking place.
- Works well for on-premise applications.
Cons
- Needs lots of training and experience.
- API scanning capability is limited and this is a problem if you develop a modern or micro-services-based application.
- It does not consistently perform grey box scans.
- No cloud platform scanning capability unlike some Netsparker alternatives.
Acunetix
Pros
- Acunetix has a wider brand reach because it was around at a time when there were few tools that could perform vulnerability scans.
- Has a friendly user interface, but key features might be considered a little incomplete for modern SDLCs.
- Allows you to configure your scans with greater detail, which is great for cyber experts, not necessarily software teams.
- Good list of integrations but many users struggle to get them working reliably.
- Provides network security features, but not as good as Tenable network security.
Cons
- Some users have become frustrated with support response.
- Limited API scanning capability.
- Licensing model can be restrictive.
- Needs lots of training to utilise its full potential unlike some Acunetix alternatives.
Metasploit
Pros
- It's reliable and provides accurate enterprise-level scanning.
- Has many plug-ins that allow you to configure multiple scans.
Cons
- Not user friendly.
- Does not have the latest vulnerabilities.
- It's time-consuming.
- Doesn't provide cloud platform scanning.

Best open source vulnerability assessment scanning tools
Open source tool can identify vulnerabilities but they may not fully meet your needs in terms of mitigation techniques offered, proactiveness of the community to update the tool as well as the cost of keeping the tool alive in your environment.

But if you really do want to go down the open source vulnerability management solution route, here are your options:
OWASP ZAP
Zap's real name is Zed Attack Proxy and contrary to some myths, it only performs web app scanning. It cannot perform mobile application security testing.
Pros
- It's an open source vulnerability scanner, therefore it's free (which has obvious cost advantages, but can be a killer when total cost of ownership is considered.
- Does many of the critical tests out of the box, but many key features are hidden behind plugins.
- Scans can run locally, so your computer might be out of action for hours on end.
- Has gray-box testing ability, although it's difficult to setup and often requires onerous custom scripting.
- Probably has the best automation feature of any open source vulnerability tool, but it also results in high false positives.
Cons
- There's very little and incomplete documentation.
- The main developers are dedicated but not great at offering help.
Support options are limited to a Google Group, but it does have active open source community support.
Difficult to integrate into an DevOps/CICD pipeline.
SQLmap
Pros
- Open source tool to find security holes with database testing.
- Limited as a full featured vulnerability management solution because it really only automates tests for SQL injections.
Cons
- The user interface is not user-friendly.
- Cannot perform complex automated vulnerability assessment for common web application and API security holes.
- Lacks support for inexperienced users.
Nmap
Pros
- Excellent for performing network vulnerability tests.
- Often used as a web vulnerability scanner but its features are limited if this is your primary aim.
- Can integrate with other tools through its plugin marketplace to extend its ability to find network vulnerabilities.
- Lots of help available online through its active community.
Nmap Cons
- Scans are complicated and take a long time and it's almost assumed that you will be dedicated security expert with lots of experience and knowledge in this field.
- Has few application vulnerability assessment features.
- Difficult to configure and requires lots of trial and error.
Wireshark
Pros
It's good at packet inspection and network security testing, but not designed to be used as a web application vulnerability scanner.
Allows you to identify network vulnerabilities.
Very good for experienced penetration testers.
Cons
The interface is complicated and you almost need an experienced buddy to guide you through the tool so that you can use it to anywhere near its full capability.
Has data payload challenges and this can make results unreliable.
Poor documentation so your learning curve will be even steeper if you've never used a security scanner previously.
Wapiti
Pros
Lightweight tool that injects payload to find security issues.
Quick vulnerability assessments but has low-res crawling technology.
Easy to get started.
Doesn't require too much training.
Cons
- Can't scan source code so comprehensive risk assessments will not be possible.
- Sometimes struggles to identify basic weaknesses, which means the results from such vulnerability detection tools are almost useless.
- Cannot be integrated with DevOps/CICD pipelines so not the best option for software development teams.
- Documentation is old and sometimes outdated, which is frustrating for new users.

How can software teams implement vulnerability management processes frictionlessly in their SDLC?
Follow this easy process to include vulnerability assessment and management in your best-practice SaaS security program:
- Run vulnerability assessment scans every time you update a production or non-production environment.
- Run scans from your CICD pipeline or on a schedule.
- Require high risk vulnerabilities to be patched within 48 hours and medium risk vulnerabilities within 1 sprint.
- Require all high and medium risk vulnerabilities to be patched before pushing a new release to prod.
- Form a team of security champions to lead this "shift left" effort.
- Track your team's vulnerability management progress and optimise as necessary.
What steps should I take to see if automated vulnerability scanning is right for my software team?
Choose Cyber Chief automated vulnerability assessment tool that provides unique web penetration testing and reveals security risks in your systems.
With this AI tool, you will discover effective ways to perform enterprise-grade application security and implement security patches really fast.
Get Cyber Chief's free trial today and ship your application with zero-known vulnerabilities.






