These days, firewalls aren’t just a part of building construction. More often, the term refers to a key component of your network security.
Firewalls work by scrutinizing incoming and outgoing traffic and allowing safe data to pass through while blocking malicious or unwanted data. Simply put, firewalls decide what traffic is allowed or not allowed based on predetermined security rules.
Without a firewall, connecting your computer directly to the open internet can expose it to several threats, such as:
- Hacking attempts
- Malware infections
- Unauthorized access to sensitive data
A firewall is your first line of defense against these cyber threats, and it’s one of the simplest ways to protect your data and network integrity.
This doesn’t mean you have to run out and purchase a firewall. In fact, you’re likely already using one as you read this article.
However, if you run a business, you might need a specific firewall device between your network and the internet.
Most People Have a Built-In Firewall
If you’re the average person, you likely have plenty of firewall protection just by using a relatively modern computer. So the need for additional hardware to protect your network might not be as pressing as you might think. This is because many devices are already protected by built-in firewalls.
In fact, you probably already have at least two layers of defense when it comes to firewalls, even if you don’t realize it.
Operating System Firewalls
Take Windows Firewall, for example. Integrated into the Windows operating system, this software firewall monitors data transmitted to and from your computer over the internet.
It works by using a set of predefined rules to determine whether to allow or block specific network traffic. By doing so, it effectively shields your system from unauthorized access and various forms of cyberattacks, like hacking attempts and malware.
Router Firewalls
Similarly, your home router is also likely equipped with its own firewall capabilities. These router-based firewalls add an additional layer of defense by overseeing the data entering and leaving your home network.
They check the data packets against a set of security criteria, blocking potentially harmful traffic while permitting safe data to pass through. This not only protects the individual devices on your network but also secures your network as a whole from external threats.
Bottom line? These two firewalls generally offer plenty of security for the average user’s needs. They give you a basic yet effective layer of security that can thwart some of the most common cyber threats. While they might not have the advanced features of dedicated hardware firewalls, for everyday internet browsing and activities, they provide adequate protection.
Types of Firewalls and How They Work
Like many things, firewalls can vary significantly in their operation and application. Let’s look at some of the most common firewalls and what they’re capable of when it comes to security.
Software Firewalls
Software firewalls are installed directly on individual devices, like your PC or smartphone. They provide a line of defense at the device level. To use an example from earlier, Windows Firewall is a software firewall.
Software firewalls are great when it comes to controlling outbound traffic to prevent malware from sending data out from your device. They also offer customizable settings, allowing you to fine-tune your security preferences, block specific applications, or open ports for certain traffic.
Hardware Firewalls
Hardware firewalls are standalone physical devices placed between a network and the gateway to the internet. They’re typically used in business environments to protect an entire network of computers.
Besides their primary function of monitoring incoming traffic, they often include additional features like VPN support and advanced traffic management. Combined with network monitoring software, these provide very comprehensive network security.
Stateless Firewalls
Stateless firewalls perform traffic filtering based purely on source and destination IP addresses and ports. For example, a stateless firewall might have a rule set to allow all traffic coming from a specific IP address (like an internal network IP) or block traffic designated for a particular port associated with known vulnerabilities.
They also treat each packet differently, inspecting it against a set of predefined rules without considering the state of the connection.
Let’s say a stateless firewall is set up to allow HTTP traffic. This means it would permit all incoming and outgoing packets on port 80 (the standard port for HTTP), regardless of the traffic’s nature or the previous packets’ history.
While they’re fast and suitable for high-traffic networks, the lack of context awareness can leave stateless firewalls vulnerable to more sophisticated cyber threats. They might not detect a malicious packet disguised as legitimate traffic from an allowed IP address or port, since they don’t consider the packet’s context within an ongoing connection. This can make them less effective against more sophisticated attacks
Stateful Firewalls
Stateful firewalls provide enhanced security by keeping track of the state of active connections. This allows them to not only filter traffic based on predefined rules but also to understand the context of traffic flows, which makes them more effective at detecting and blocking malicious activities.
Basically, since stateful firewalls can track and remember the history of each connection, they’re able to make more informed decisions about allowing or blocking traffic.
For example, if a user inside the network starts a web browsing session, a stateful firewall will note the outgoing request and recognize the incoming response as part of the same session. This context awareness allows the firewall to permit legitimate responses to user requests while blocking unsolicited incoming traffic.
Stateful firewalls can also recognize patterns indicative of cyberattacks, such as unusual data payloads or attempts to exploit specific vulnerabilities in the network, and respond by blocking these activities.
Overall, these firewalls are great in environments where security requirements are high.
Hosted (Cloud) Firewalls
The main advantage of cloud-based firewalls is that they offer flexibility and scalability. They’re great for businesses with cloud-based infrastructure or those that require remote access capabilities.
Hosted firewalls can be easily scaled up or down based on demand, and they offer the advantage of being managed by service providers, reducing the burden on in-house IT teams.
They’re particularly effective in protecting against distributed denial-of-service (DDoS) attacks and managing remote user access. If you run a large enterprise, this is the way to go.
Virtual Firewalls
Virtual firewalls are designed for virtualized environments, such as those used in data centers or cloud platforms. They provide similar functionalities to traditional firewalls but are optimized for virtual networks.
Say you’re a cloud-based service provider with multiple virtual machines (VMs). If you host different applications on separate VMs within the same physical server, a virtual firewall can ensure that your traffic is appropriately segmented, preventing a security breach in one application from affecting others. It prevents you from having a single point of failure.
These firewalls can enforce security policies across virtual machines and can be dynamically allocated to different parts of a virtual network, offering tailored protection that adapts to the virtual environment’s unique demands.
Check Windows Firewall Status
As we mentioned earlier, the native software firewall on your device offers plenty of protection for most people. If you run Windows, this would be Windows Firewall, or Windows Defender Firewall. It’s a stateful firewall, which means it has the intelligence to monitor and control the flow of incoming and outgoing network traffic based on understanding the connections’ context.
This sets Windows Defender Firewall apart from basic, stateless firewalls, as it can remember the state of network connections and use this information to decide whether to allow or block traffic.
It will examine data packets traversing through your network, categorizing them as legitimate data or potential threats. It’s a pretty robust tool for both home and professional settings.
It also has a fair amount of customization functionality. It can be configured to prohibit specific applications from accessing the internet, allowing exceptions for trusted programs, and managing network traffic based on various protocols and port numbers.
In some professional settings, enabling this firewall might be a prerequisite for accessing network resources securely. At home, it’s also a good idea to have it running just for basic security.
So how do you check the status and turn it on?
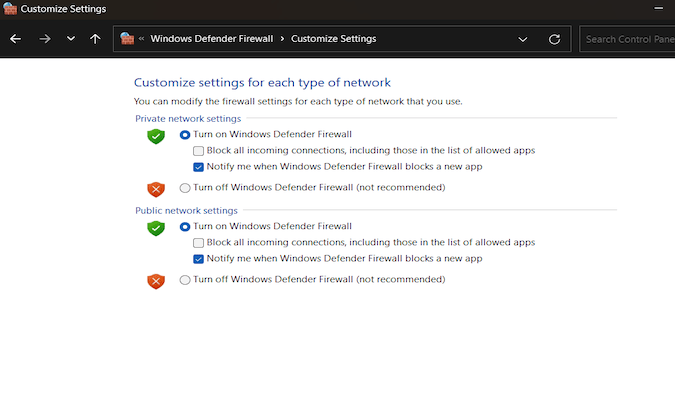
To activate Windows Defender Firewall, follow these steps:
- Access Your Control Panel: Click on the Start menu (it will typically have the Windows logo) and type Control Panel. Open the Control Panel, which is the central hub for various system settings and configurations.
- Navigate to Firewall Settings: In your Control Panel, select System and Security, which houses several important security features of your system. Under this category, click on Windows Defender Firewall. This will open the firewall’s dashboard, where you can view its current status and modify its settings.
- Adjusting Firewall Options: Look for the option labeled Turn Windows Defender Firewall on or off on the left side of the window. This allows you to check and customize the operational status of your firewall.
- Enable Firewall Protection: In the new window, you’ll see settings for different network types – Domain, Private, and Public. For each of these network types, select the option Turn on Windows Defender Firewall.
Final Thoughts
With cyberattacks and hacking on the rise, firewalls are a necessity today. Depending on your needs, you can choose from built-in software firewalls like Windows Defender Firewall, or more complex hardware and stateful firewalls.
For most users in home and small business environments, the built-in firewall capabilities provided by operating systems and routers offer enough protection. Just make sure your firewall is properly configured and regularly updated.
Keeping your firewall active and well-configured is one of the simplest, most effective steps you can take to protect your computer. But it’s still just a first line of defense. For a full-stack security strategy, consider using network monitoring software and other tools.















