We live in a world where data breaches are not a question of if, but a question of when.
Data breaches are on the rise for the third consecutive year, and all the signs point to a continuation of this trend in 2022/2023.
With this in mind, a primary goal for any Salesforce implementor is to ensure the safety and security of their Salesforce orgs; but to do so, a realistic approach to Salesforce security needs to be taken.
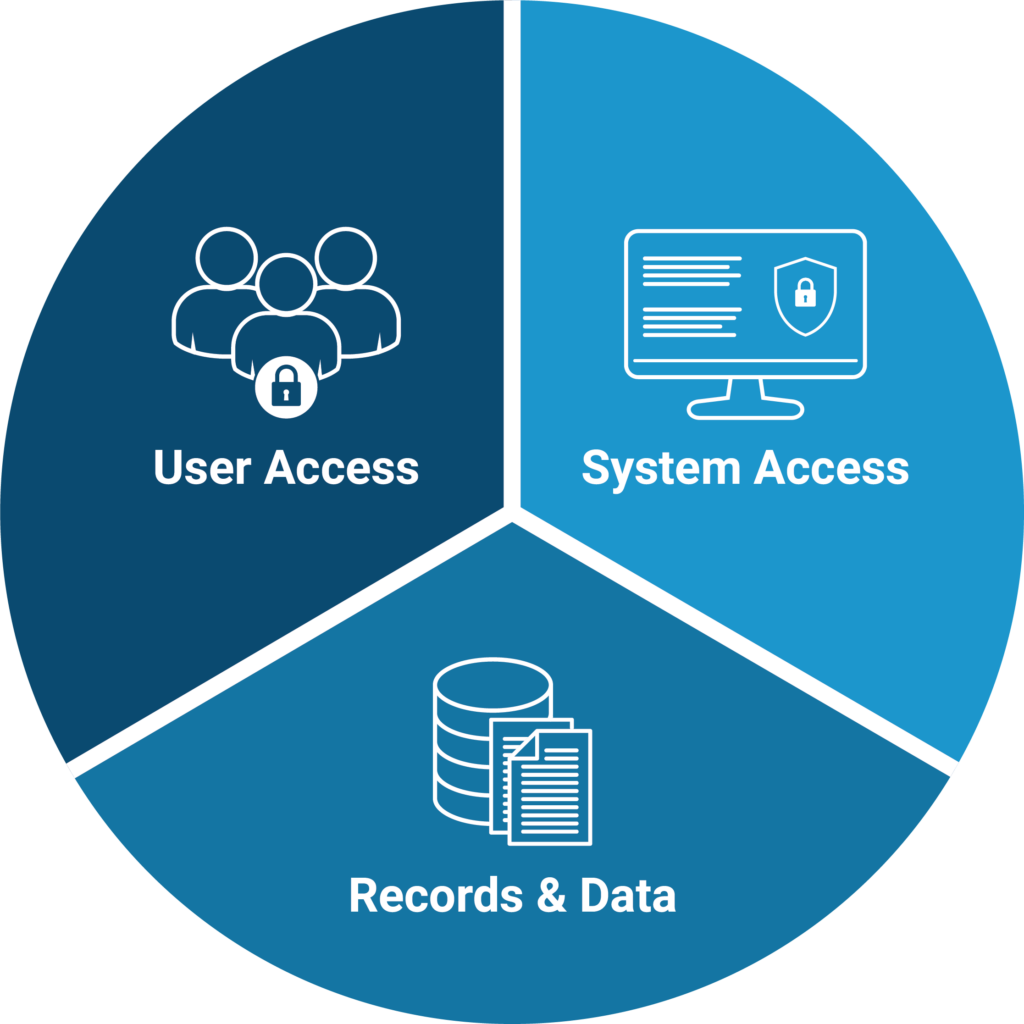
Simply focusing on password complexity and frequent password updates is no longer enough (and also creates unnecessary frustration for users). Instead, we recommend strengthening Salesforce security within your org by implementing the Three Pillars of Salesforce Security:
User Access: Don’t Give People Access they Don’t Need
Take the time to understand what constitutes full admin access. Just because a user isn’t set up with a full System Admin profile does not mean that they do not have full Admin access. Be very careful when distributing access to users and make sure you’re auditing this access on a regular basis.
System Access: Don’t Give Systems Access they Don’t Need
Review the systems that have access to your Salesforce data and verify that they have the proper level of access. The vast majority of third party systems should not be able to delete records, update Salesforce user info, update transactional records, or access Personal Identifiable Information (PII).
Records & Data: Don’t Keep Records/Data you Don’t Need
Holding on to records you don’t need can be very expensive and raise liability issues. Your company almost certainly has data retention and deletion policies. Review those policies and make sure that your Salesforce org is aligned with the specifics of the policies. (If you DON’T have a policy – now would be a good time to create one. Here’s a template to help with that.)
Want to know more about each of these pillars? Good news. We’ll have a new post every week for the next 3 weeks diving into more detail on each of the pillars.
In the meantime, if you want to do some brushing up on Salesforce Security best practices, check out this blog. Have questions? Want to connect? Get in touch. We’d love to hear from you.